The definitive cyber security checklist you need for data protection

Cyber threats are currently on the rise, and no one wants to fall victim to data breaches or cyber-attacks. But don't worry, with the right measures in place, you can significantly reduce the risk and safeguard your sensitive information. To help you increase your security defenses, this article presents a definitive cyber security checklist that includes essential steps for effective data protection.
But before we dive into the nitty-gritty of the checklist, let's first define cyber security and its significance for businesses.
What is cyber security?
Cyber security refers to the measures and practices taken to protect computer systems, networks, and data from unauthorized access, attacks, and damage. In simpler terms, it's like a shield that safeguards our digital world against malicious activities and keeps our information safe. It involves a range of strategies, technologies, and best practices aimed at preventing and mitigating the risks posed by cyber threats, like hackers, viruses, and data breaches.

The importance of cybersecurity for businesses
Cybersecurity is extremely important to businesses for several reasons:
Defense against cyber threats
The threat landscape is constantly evolving, and cybercriminals are getting smarter every day. That's why you need to be proactive in defending your business against various threats like viruses, scams, tricks, and even insider threats. Having a strong cybersecurity strategy in place can help identify, stop, and handle these threats effectively. Implementing insider threat software is an important aspect of protecting against compromised or malicious employees.
Protection of sensitive data
Your business may be handling vast amounts of sensitive data, including customer information, financial records, trade secrets, and proprietary data. Making sure this info stays safe and secure is crucial. With a solid cybersecurity system in action, you can prevent unauthorized access and data breaches, which not only protects the reputation of your business but also keeps your customers feeling secure. Implementing secure KMS for enterprises is a vital component of a robust cybersecurity strategy, ensuring the protection of sensitive data and maintaining the trust of your customers.
Prevention of financial loss
Cyberattacks can have severe financial implications for businesses. Ransomware attacks, data breaches, and fraud can result in significant financial losses, including direct costs for incident response, legal fees, regulatory fines, and potential lawsuits. Moreover, the loss of customer trust and business opportunities has the potential to hurt your business financially in the long term.
Compliance with regulations
Many industries are subjected to stringent regulatory requirements concerning data protection and privacy. Failing to adhere to cybersecurity compliance can lead to substantial penalties and reputational damage. Implementing effective cybersecurity measures secures your business’ adherence to applicable regulations, such as the General Data Protection Regulation (GDPR).
Essential elements to include in your cyber security checklist
Learn some practical tips and actionable guidelines to enhance your cyber security posture. From securing devices and networks to implementing robust passwords and encryption techniques, this cyber security assessment checklist has everything covered.
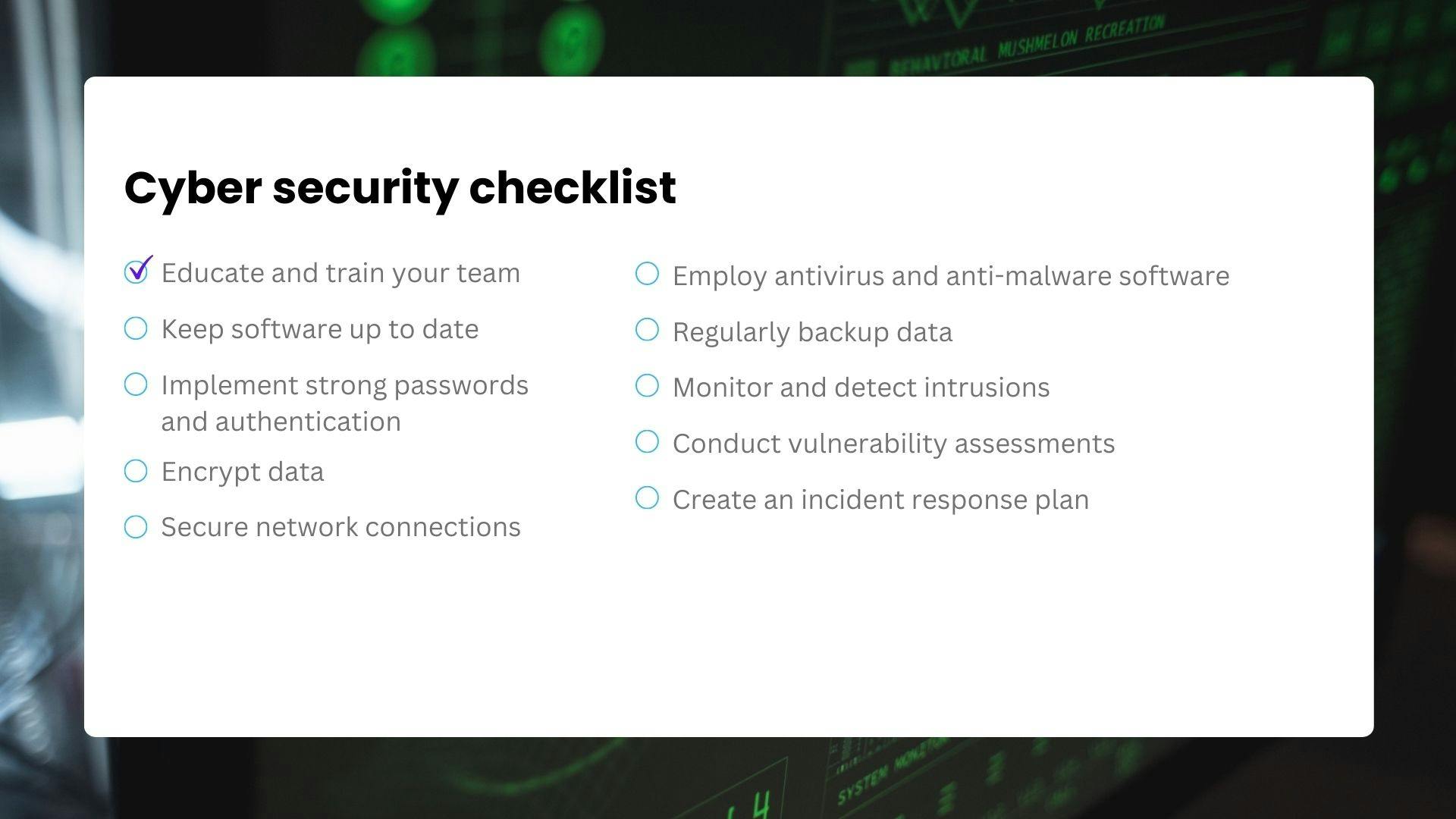
Here's a deeper dive into this cyber security checklist:
1. Educate and train your team
Human error is often a weak link in cybersecurity. According to cyber security statistics in 2022 alone, 74% of all data breaches involve a human error.
For this reason, it’s vital that you and your team are well-educated and trained on best practices for data protection. Make sure that your workforce knows how to recognize and avoid phishing attempts, suspicious links, and email scams. Conducting regular cyber security awareness training sessions will also promote a culture of cybersecurity within your organization.

Take the proactive step towards a secure future for your business. Use EdApp to empower your workforce with essential cyber security training.
2. Keep software up to date
Keeping your software up to date is essential for maintaining a cyber compliance digital environment. Regularly update your operating system, web browsers, and applications to ensure you have the latest security patches and bug fixes. Software updates often address vulnerabilities that hackers could exploit to gain unauthorized access to your data.

3. Implement strong passwords and authentication
Another vital step in data protection is implementing strong passwords and authentication mechanisms. It’s important that you and your staff use complex passwords comprising a mix of uppercase and lowercase letters, numbers, and symbols.

If needed, consider using a password manager to securely store and manage your organization’s passwords. Additionally, enable multi-factor authentication (MFA) whenever possible and enable DMARC policy to add an extra layer of security. Some password manager tools can even manage all credentials and authentication protocols you implement in one place.
4. Encrypt data
Data encryption is an effective method to safeguard sensitive information. Encrypt your data both at rest and in transit. Encryption makes sure that even if your data is intercepted or stolen, it remains unreadable and unusable without the decryption key.

5. Secure Network Connections
Securing your network connections can go a long way in preventing unauthorized access to your data. Make sure that your Wi-Fi network is password protected and encrypted with WPA2 or WPA3 encryption protocols. Encourage your staff to avoid using public Wi-Fi networks for transmitting sensitive information, as they're susceptible to eavesdropping and man-in-the-middle attacks.

6. Employ antivirus and anti-malware software
Installing reliable antivirus and anti-malware software is essential for detecting and preventing malicious software infections. Regularly update your security software to make sure it can effectively identify and mitigate the latest threats.

7. Regularly backup data
Regular data backups are critical for data protection and recovery in the event of a cyber incident or system failure. Implement automated backup solutions that store your data in secure off-site locations. Regularly test your backups to ensure their integrity and reliability.

8. Monitor and detect intrusions
Implement intrusion detection and prevention systems (IDS/IPS) to monitor your network for any unauthorized activities or potential security breaches. These systems analyze network traffic patterns and behavior to identify and block malicious activities in real time.

9. Conduct vulnerability assessments
Regularly perform vulnerability assessments and penetration testing to identify potential weaknesses in your systems and networks. Address any vulnerabilities promptly to prevent them from being exploited by attackers.

10. Create an incident response plan
Having an incident response plan in place makes sure that your organization has a coordinated and efficient response in the event of a cyber incident. Define roles and responsibilities, establish communication channels, and outline the steps to be taken to mitigate the impact of an incident and restore normalcy.

Strengthen your cyber security with EdApp
Cybersecurity is an ever-evolving field, with new threats emerging constantly. Having a team that’s informed and educated about the latest cyber threats, security best practices, and industry trends will get your organization one step ahead of cybercriminals.
For your cyber security training, look no further than EdApp. This cyber security training platform offers a comprehensive range of cybersecurity training courses for beginners and experts, all designed to raise awareness about various aspects of cybersecurity.
They have courses on general Cyber Security and Cyber Security Awareness, which cover topics such as safe security practices, phishing attacks, social engineering, sensitive data exposure, and more. Designed in bite sizes, your team will be able to complete this training without disrupting their daily work routines. Even better, they can access them again for a knowledge refresh using any device they prefer.
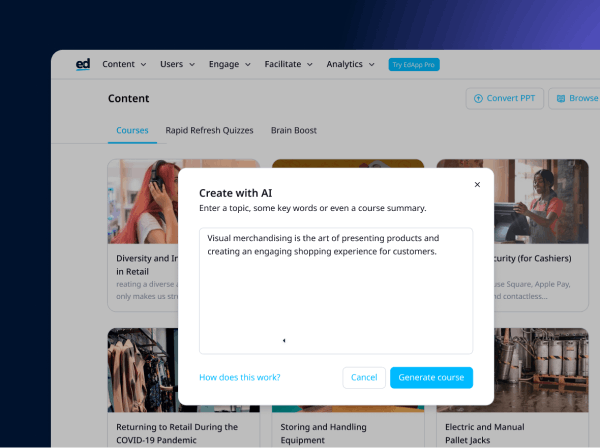
You can also use EdApp’s Create with AI tool if you want to build cyber security courses that are not in the library yet. The great thing about this tool is that it automates most of the tasks involved in creating a course, from writing content to designing visuals. All you need to do is pop in your cyber security lesson ideas, and the tool will instantly give you a fully packaged training course.
To evaluate the effectiveness of cybersecurity training and measure your employees' progress, EdApp has built-in practical assessments and a robust analytics suite. These features allow you to assess your team’s understanding of key concepts, identify areas that require further reinforcement, and track their overall performance. By monitoring their progress, you can identify any gaps in knowledge and take proactive measures to address them.
Boost your organization's overall security posture with EdApp. Start training your team on cyber security today!
Author
Jen Avelino
Jen is a learning expert at SC Training (formerly EdApp), a mobile-based training platform that helps corporates and businesses bring their training solutions to the next level. She carries an extensive writing experience in a variety of fields, including architecture, the gig economy, and computer software. Outside of work, she enjoys her free time watching her favorite series and documentaries, reading motivational books, and cross-stitching.
